WIFI hack using kali linux ( Fern-wifi-cracker ) :
 In this post i will show you how we can hack any type of WIFI encryption easily in just few click no more coding , this is all possible just because of fern-wifi-cracker software in KALI LINUX . But let me give short description about this software :
In this post i will show you how we can hack any type of WIFI encryption easily in just few click no more coding , this is all possible just because of fern-wifi-cracker software in KALI LINUX . But let me give short description about this software :
Fern wifi cracker is a wireless security auditing application that is written in python and uses python-qt4. This application uses the aircrack-ng suite of tools.
Disclaimer: I carried out this attack using my own WIFI network, all MAC Addresses and names have been faked. This tutorial is for learning purposes only and should not be used for any illegal activities.Don't break someone privacy who not belongs to you , im not liable for any illegal activity.......
[ If you are newbie in hacking WIFI then please goto my previous post and read about basics of Hacking WIFI ]
[ All bold letter are command to type ]
------------------------------------------------------------------------------------------------------------------------------
# FOR WEP ENCRYPTION :
Step 1 : Start KALI LINUX and open terminal as root .
Step 2 : In terminal
Type : "fern-wifi-cracker" orGoto -->> Applications --> Kali Linux -> Wireless tools -->> Fern-wifi-cracker . It will open like this
Step 3 : Now as you can see in image
1 : Select wireless card for monitor mode at "step 1 in image"
2 : Click to Active wifi AP scanner at "step 2 in image" 3 : Click on WEP option at "step 3 in image"
Step 4 : Now select target AP as shown in image.Click on regular attack ,then click attack
Tip : You can also select different attack mode ( you should know what you are doing , if you want to know about attack modes then check my post )
In my case i used caffe latte attack , and cracked WEP Encprytion in just 1min 25 seconds only.
After few mins when process is finished you can see the key as shown in image.
-----------------------------------------------------------------------------------------------------------------------
# FOR WPA & WPA2 ENCRYPTION :
Step 1 : Start KALI LINUX and open terminal as root .
Step 2 : In terminal
Type : "fern-wifi-cracker"
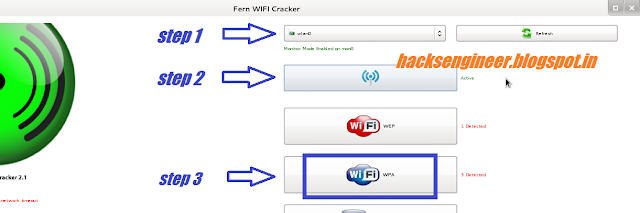
Step 3 : Now as you can see in image
1 : Select wireless card for monitor mode at "step 1 in image"
2 : Click to Active wifi AP scanner at "step 2 in image"
3 : Click on WPA option ( in blue at step 3 )
Step 4 : Selct your target :
1 : Now select AP as shown in image then click on regular attack.Click on Browse option and navigate to your password list ( dictionary file ).
2 : Click attack.
# As you can see in the image i cracked WPA2 password successfully .
---------------------------------------------------------------------------------------------------------------------------
# FOR WPS :
Step 1 : Start KALI LINUX and open terminal as root .
Step 2 : In terminal
Type : "fern-wifi-cracker"
Step 3 : Now as you can see in image
1 : Select wireless card for monitor mode at "step 1 in image"
2 : Click to Active wifi AP scanner at "step 2 in image"3 : Now select Encryption type from WEP or WPA at " step 3 in image "
Step 4 : After selecting Encryption type just , follow as shown in image
It will take 1 - 7 hour after then it will show WPS pin , you can use it as password.
Conclusion : From above demonstration you can understand nothing is secure everything is breakable now you all are thinking what to do , to save yourself for being hacked by someone , goto my post about basics of hacking. Example : Here i created my shutdown prank but i changed it's icon as internet explorer icon.Also named internet explorer.
Example : Here i created my shutdown prank but i changed it's icon as internet explorer icon.Also named internet explorer.

































